


















 |


 Success Criteria, Risks, Capabilities
for PIN
Success Criteria, Risks, Capabilities
for PIN
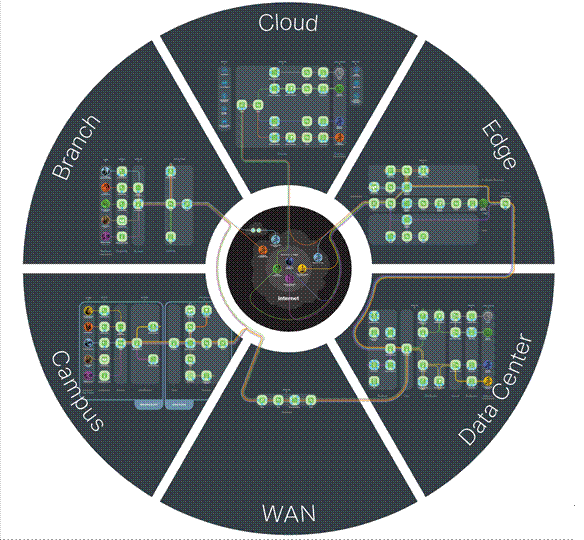
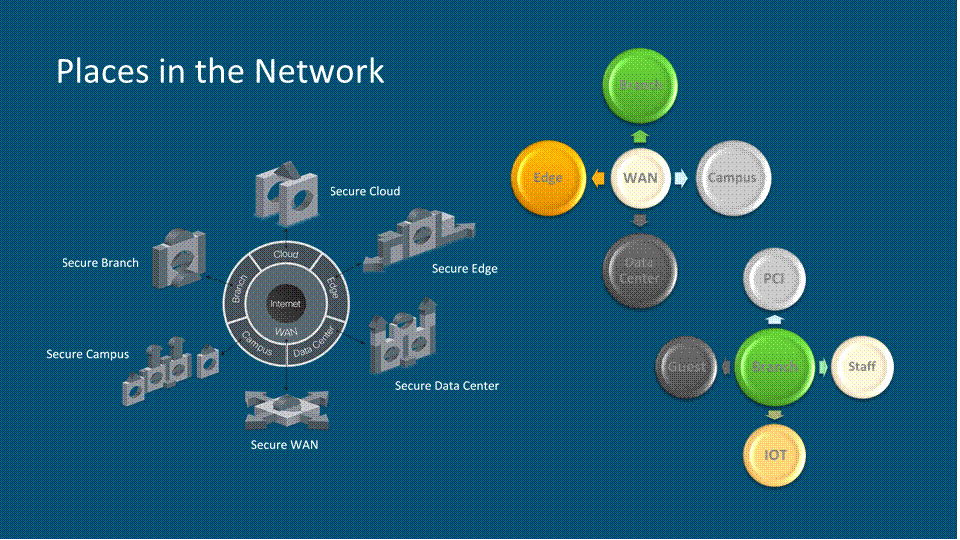
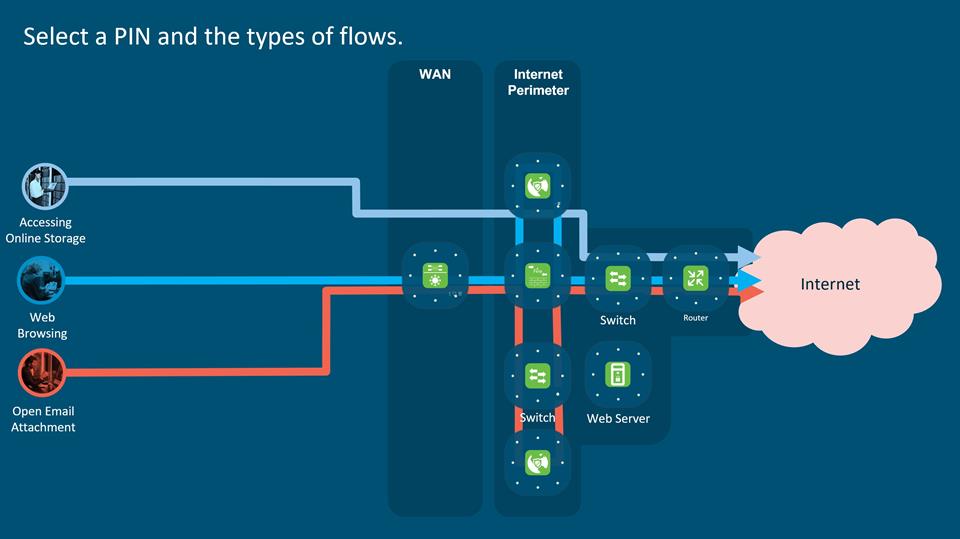
PIN: Internet Gateway
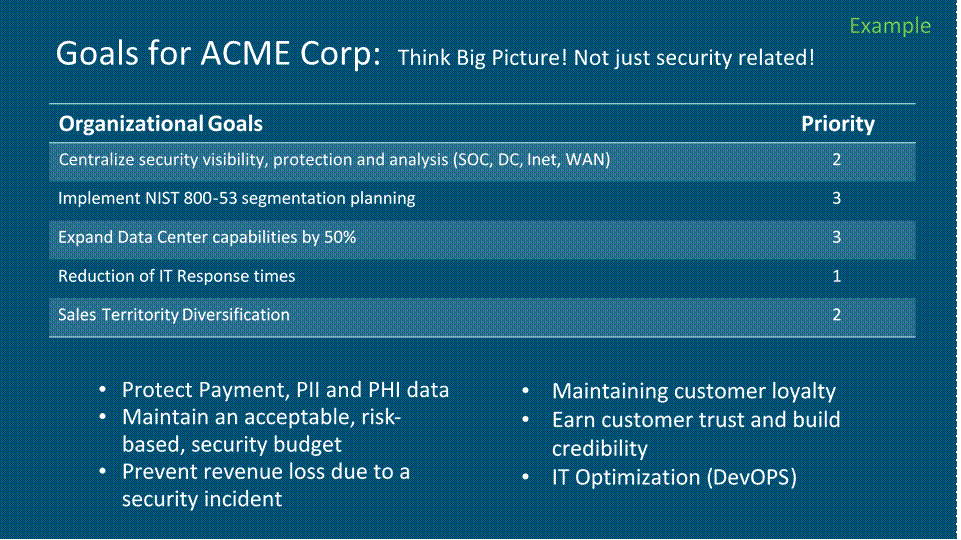
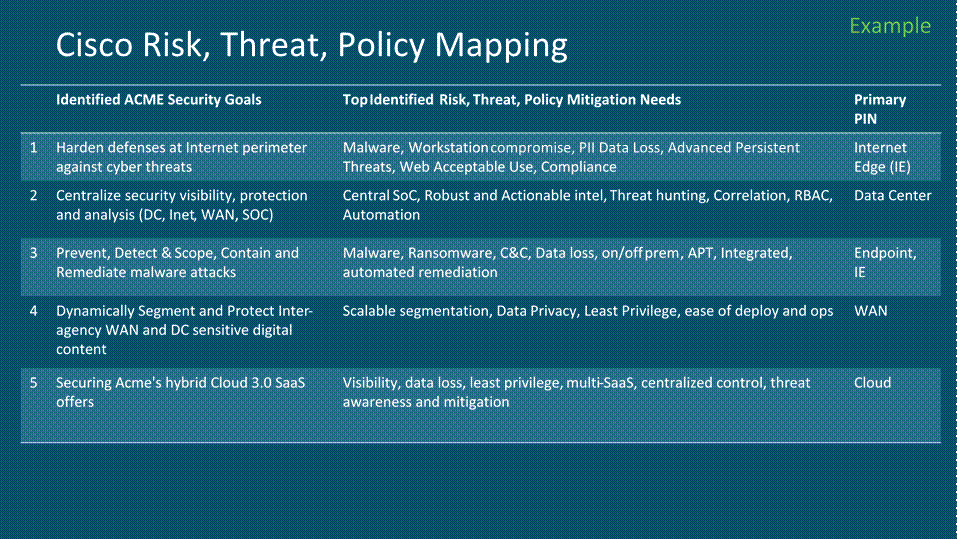
Priority Success Criteria / Risks Top Identified Risk, Threat, Policy
1 Harden defenses at Internet perimeter Malware, Workstation compromise, PII Data Loss, Advanced against cyber threats Persistent Threats, Web Acceptable Use, Compliance
4 Centralize security visibility, protection Central SoC, Robust and Actionable intel, Threat hunting, and analysis (DC, Inet, WAN, SOC) Correlation, RBAC, Automation
3 Prevent, Detect & Scope, Contain and Malware, Ransomware, C&C, Data loss, on/off prem, APT,
Remediate malware attacks Integrated, automated remediation
5 Dynamically Segment and Protect Scalable segmentation, Data Privacy, Least Privilege, ease of
Inter-agency WAN and DC sensitive deploy and ops digital content
2 Securing Acme's hybrid Cloud 3.0 SaaS Visibility, data loss, least privilege, multi-SaaS, centralized control, offers threat awareness and mitigation
Example
Compensating Capability
Firewall, IPS, DNS sec, C&C, Url
Filtering, web security, anti-malware
Investigate, Stealthwatch, ATA, ISE,
Threat Awareness Service, AMP4E, CloudLock
Anti-malware, Sandboxing, file reputation, C&C mitigation, IPS, web security, DNS security
Segmentation, access control, FW, IPS, AM, VPN, analytics, behavior analysis
DLP, email security, anti-phishing, public cloud protections, encryption, Access Control, insider threat